Industrial Security


Safety in the industrial environment was synonymous with operational safety for a long time. Even today, a machine or plant is considered safe if it is running without malfunction and without danger for the user. In automated production this safety term is no longer sufficient. The communication networks which make automation even possible raise own questions about safety. They are considered safe when they are protected against unauthorised access. Conversely, operational safety in automated production is only ensured when there is network security. To draw the line between the two safety terms, one speaks of "industrial safety" and "industrial security" in English:
Averting of danger encompasses all measures that protect communication networks of automated production plants from unauthorised access. Beginning with physical access protection and special operating procedures based on guidelines or check lists up to the technical protection of the communication networks and systems. Measures for information technology (IT for short) cannot be simply transferred to operational technology (OT for short). Whereas IT network of the control levels are sealed off to the outside world by firewalls, virus protection, web filter, data encryption and much more, automation increasingly requires that controllers, devices and sensors can communicate with each other with as few barriers as possible at the field level. That is why the concept of the trusted zone is valid till now for many OT networks: Within a specified area that is secured to the outside, all network devices are deemed as trustworthy and communication between them is not controlled.
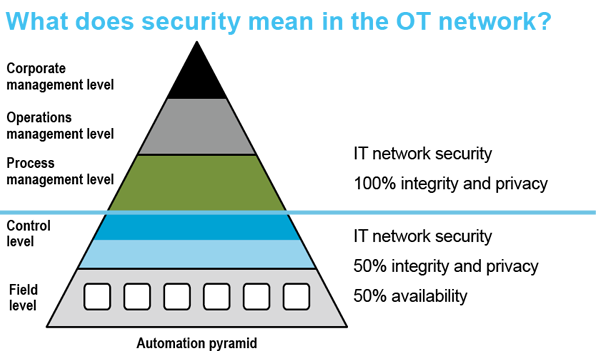 Automation pyramid: IT security vs. OT security
Automation pyramid: IT security vs. OT security
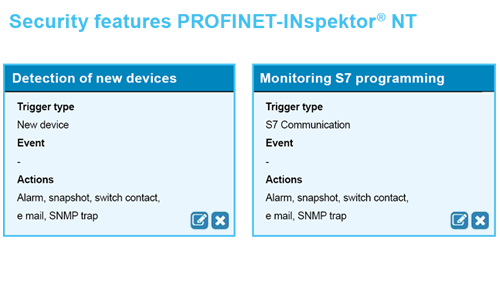 Security in the PROFINET: Recognise abnormalities in time
Security in the PROFINET: Recognise abnormalities in time
Security in the trusted zone is precarious, however, in two aspects: On the one hand, because unauthorised accesses are also possible within the trusted zone onto control cabinets, network ports or programming accesses. On the other hand, because own or visiting service employees cause security-relevant incidences – possibly even unintentionally, by supposedly harmless actions such as a network scan or the loading of firmware updates. Against this background, the industry is relying increasingly on more robust devices that have proven their insensitivity towards load peaks in certification processes (e.g. Net Load Class for PROFINET).
With the advance of PROFINET and further Ethernet-based networks, security in the OT network is facing new challenges, however. The real-time communication channels contribute significantly to the increasingly greater data amounts that flow into the production process which are retrieved from the controller levels or are even sent directly from the customer via the Internet to the field level. Under these conditions a reliable network security can only be ensured it the data traffic remains replicable at any time – according to the basic principle: Who communicated what, when to whom by which channel?
The Permanent Network Monitoring (PNM) developed by Indu-Sol provides precise answers for that. Even in the PROFINET, where an unforeseeable amount of acyclic data traffic is added to the cyclic data traffic, the total communication can be evaluated, analysed and archived accordingly. Based on the collected status data, the PNM can warn against irregularities in the network in time, which not only makes preventive maintenance easier but also serves to cover security requirements. Based on the status data, attacks from the inside can thus be traced as well.
The current version of the PROFINET-INspektor® NT and the software PROmanage® NT make it therefore possible for the first time to record abnormalities that concern OT security: On the one hand, INspektor® detects every programming access into the controller; on the other hand he recognises the presence of unknown device in the network. With that, the diagnostic device provides decisive information immediately to the operators in serious cases – because you can react appropriately only if you know you are being attacked. The messaging of all security-relevant events is carried out, depending on configuration, via e-mail, messaging serving, OPC or SNMP to the respective responsibility range; literally "unbureaucratically". The collected data can be retrieved down to the minute then from the network chronology of PROmanage® NT for a whole year.
In the knowledge database, we answer the most frequently asked questions about our hardware and software.
Stay informed! Receive the latest offers and news about industrial networks and their optimization - conveniently via e-mail.
PROFINET - The Movie | Technology Made Easy
Take a look!
